

Have you ever received an email from someone you knew asking you to buy gift cards out of nowhere? Or a message from an unnamed administrator saying your account is going to be deleted if you don’t renew your information? In today’s digital age, cyberattackers commonly try to pretend to be someone you know or trust to persuade you to hand over important information. The methods they use to impersonate others can vary widely, but by staying alert and aware, you can spot these illegitimate emails before they can do any harm. Here are a couple of examples the Metropolitan State University of Denver Information Technology Services security team has been seeing a lot of lately:
Job-offer scams
An email about part-time job opportunities.
Here’s an example: The contact info in the body of the email is the first thing that should catch your attention. Any time an external address is tied to a job offer or other enticement, users should confirm the validity of that account with Human Resources, ITS or the purported internal department that is listed. Do not use any of the information in the email itself — don’t call the numbers, reply to the email or follow any links. Instead, look up the appropriate departments using official MSU Denver resources, such as the official MSU Denver website or internal Office 365 address book
Also notice whether the message is coming from a legitimate MSU Denver email account — you can tell from the @msudenver.edu email domain. If the account of someone at MSU Denver is compromised as part of a phishing scam, that account may be used to send out a new wave of phishing messages, now with the added credibility of coming from a legitimate internal account. Remember, always verify the contents of a suspicious email before acting on it, no matter whom it appears to be coming from.
Fake document links
File-hosting services such as Google Docs and Docusign send automated notifications to recipients of a shared document. Scammers can use these systems to send malicious links under the guise of a shared document — or even just send a message formatted to look like such a notification. Here’s an example:
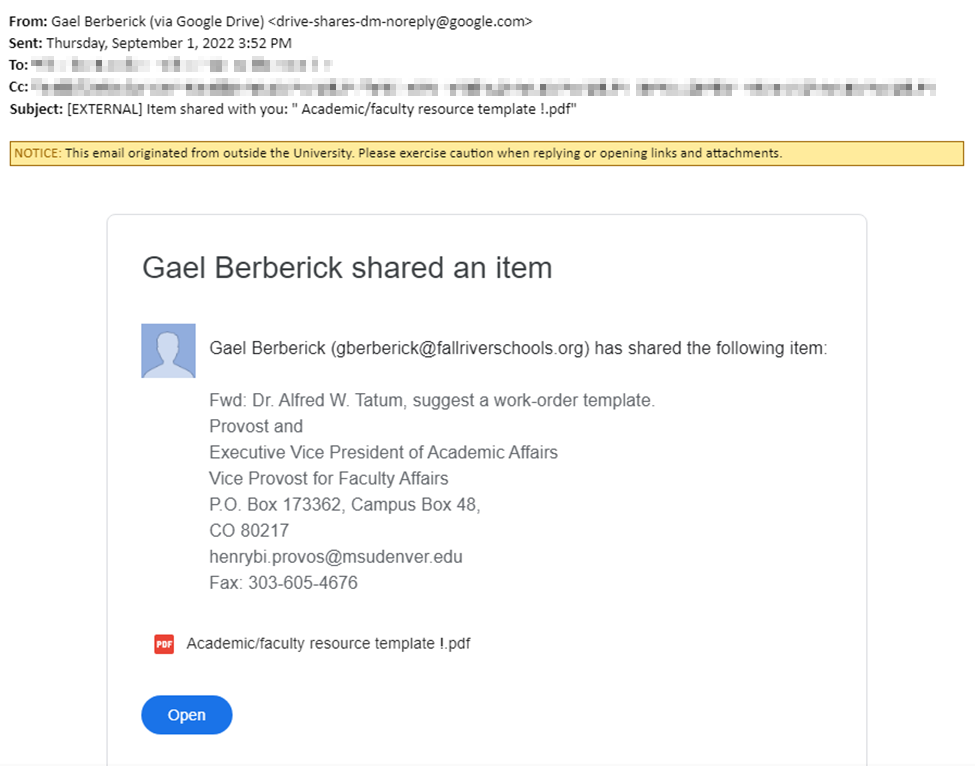
Such messages may come with a request to review, sign or otherwise interact with the attachment. Assuming legitimacy, a victim may open the provided link, whereupon they’re brought to a login prompt that looks like the one for that service. But this, too, is a trick on the part of scammers, a way to persuade people to unwittingly hand over their login credentials (and maybe other information, too).
Blocking messages such as this (when being sent by legitimate platforms such as Google Drive) would be impractical and counterproductive since the services are also used by legitimate parties. Thus, users need to be vigilant when opening attachments from outside sources. If you are not expecting the attachment, or the information you’re being shown doesn’t all line up, verify with the sender through other channels.
These are just two examples of phishing attacks, but new and remixed approaches are being seen all the time. If you spot anything suspicious, don’t be afraid to double-check with the sender. A brief double-check might be inconvenient sometimes, but it’s worth it to keep employee, student and University information secure.
And, as always, if you’ve identified an illegitimate message or can’t verify it yourself, please forward it to [email protected]. The MSU Denver IT Security Team investigates all messages sent to this address for legitimacy and can use that information to better safeguard the University by proactively blocking unsafe addresses, websites and attachments.

